Professional Documents
Culture Documents
0 ratings0% found this document useful (0 votes)
14 views70-410 r2 Lecture Slides Lesson 10
70-410 r2 Lecture Slides Lesson 10
Uploaded by
hhhhhCopyright:
© All Rights Reserved
Available Formats
Download as PPTX, PDF, TXT or read online from Scribd
You might also like
- Practice Testanswers 6Document6 pagesPractice Testanswers 6Marina GeorgiouNo ratings yet
- Data Comm Part 2.ppt NewDocument48 pagesData Comm Part 2.ppt Newmuhabamohamed21No ratings yet
- CH5Document58 pagesCH5digafeeyuelNo ratings yet
- IP AddressingDocument29 pagesIP AddressingcsebitannaNo ratings yet
- CCNA1 Chapter 6Document6 pagesCCNA1 Chapter 6mubaswirNo ratings yet
- IPv4 ReportDocument34 pagesIPv4 ReportGWYNETH DIOGRACIASNo ratings yet
- Chapter 4 Part IDocument86 pagesChapter 4 Part Ianebek555No ratings yet
- IP Addressing: Introductory MaterialDocument26 pagesIP Addressing: Introductory MaterialRajurajiNo ratings yet
- Mod 03Document56 pagesMod 03michael.santiago15No ratings yet
- Unit 4. NetworkingDocument31 pagesUnit 4. Networkingbca2022jagranNo ratings yet
- CN Unit 2Document49 pagesCN Unit 2Prakhar MishraNo ratings yet
- 98-366 MVA Slides Lesson 4Document31 pages98-366 MVA Slides Lesson 4cvigaNo ratings yet
- CCNA1 Chapter 6 Practice Test Questions: SW 7/31/2012 /var/www/apps/conversion/current/tmp/scratch430/105029902.doc 1Document6 pagesCCNA1 Chapter 6 Practice Test Questions: SW 7/31/2012 /var/www/apps/conversion/current/tmp/scratch430/105029902.doc 1Ramel PoliusNo ratings yet
- Chapter 4 Part 1Document25 pagesChapter 4 Part 1FantaNo ratings yet
- CCNA1 Chap6 Practice TestquestionsDocument6 pagesCCNA1 Chap6 Practice TestquestionsAnhTuan LeNo ratings yet
- IPV4 and IPV6: Presented by Ye Kyaw Thein M.SC (Physics), M.I.ScDocument41 pagesIPV4 and IPV6: Presented by Ye Kyaw Thein M.SC (Physics), M.I.ScMie NgeNo ratings yet
- L06 NetworkLayer PartIIDocument54 pagesL06 NetworkLayer PartIITerence YapNo ratings yet
- Instructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Document28 pagesInstructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Nuhamin BirhanuNo ratings yet
- Chapter 4 Part I - 220121001702Document86 pagesChapter 4 Part I - 220121001702zerihun nanaNo ratings yet
- 3 IPv4 Part2Document38 pages3 IPv4 Part2Easha AsifNo ratings yet
- IP Addressing: Introductory MaterialDocument26 pagesIP Addressing: Introductory MaterialAamer ZahoorNo ratings yet
- Adresarea IPDocument80 pagesAdresarea IPgheorghe_georgelNo ratings yet
- File 034Document25 pagesFile 034Zulkernain Omer TariqNo ratings yet
- ITN instructorPPT Chapter8Document88 pagesITN instructorPPT Chapter8Paul BryanNo ratings yet
- Advanced IP AddressingDocument14 pagesAdvanced IP AddressingVictor BittarNo ratings yet
- Module 11: Ipv4 AddressingDocument44 pagesModule 11: Ipv4 AddressingLuthfie NaufaldoNo ratings yet
- NB instructorPPT Chapter7 FinalDocument89 pagesNB instructorPPT Chapter7 FinalSergio MedinaNo ratings yet
- Ip AddressingDocument83 pagesIp AddressingGetnete degemuNo ratings yet
- BEnny AzDocument8 pagesBEnny AzastaylerrNo ratings yet
- IP Addressing: (Ipv4 Addresses)Document35 pagesIP Addressing: (Ipv4 Addresses)Kumail RazaNo ratings yet
- NDC Chapter 1Document10 pagesNDC Chapter 1Miraj SherifNo ratings yet
- CN - Chapter 5 - The Network Layer - Class 3, 4Document24 pagesCN - Chapter 5 - The Network Layer - Class 3, 4himanshuajaypandeyNo ratings yet
- IPV4 and Subnetting StrategyDocument39 pagesIPV4 and Subnetting StrategyrolandsabitNo ratings yet
- chapter3-IP AddressingDocument47 pageschapter3-IP AddressingmulugetaNo ratings yet
- IP Addressing: Presentation - ID © 2008 Cisco Systems, Inc. All Rights Reserved. Cisco ConfidentialDocument40 pagesIP Addressing: Presentation - ID © 2008 Cisco Systems, Inc. All Rights Reserved. Cisco Confidentialnathaniel manuzonNo ratings yet
- Introduction To Ip AddressDocument22 pagesIntroduction To Ip AddressMetsi KinNo ratings yet
- Take Assessment - Enetwork Chapter 6 - Ccna Exploration: Network Fundamentals (Version 4.0) - Answers - 2012 - 2013Document7 pagesTake Assessment - Enetwork Chapter 6 - Ccna Exploration: Network Fundamentals (Version 4.0) - Answers - 2012 - 2013Alexander Henao GutierrezNo ratings yet
- Network Subnetting 4 PDFDocument6 pagesNetwork Subnetting 4 PDFEdison Jr. GaudicosNo ratings yet
- CN Lab 3Document12 pagesCN Lab 3talha khalidNo ratings yet
- Network ConfigurationDocument22 pagesNetwork Configurationapi-556424124No ratings yet
- ReS1.08 IP ADDRESSING ARCHITECTUREDocument14 pagesReS1.08 IP ADDRESSING ARCHITECTUREHisham MohamedNo ratings yet
- Ip AddressingDocument38 pagesIp AddressingFadilMaulanahNo ratings yet
- CCNA 1 v3.0 Module 9 TCP/IP Protocol Suite and IP AddressingDocument33 pagesCCNA 1 v3.0 Module 9 TCP/IP Protocol Suite and IP AddressingPŘincê ÂĻĩNo ratings yet
- Lec 7 - IP AddressDocument60 pagesLec 7 - IP AddressMUBEEN LIAQATNo ratings yet
- Ipv4 Con GurationDocument5 pagesIpv4 Con GurationLaura DeeNo ratings yet
- Chapter - 7Document99 pagesChapter - 7Sindhu official radhakrishnNo ratings yet
- Classless Inter Domain Routing (CIDR) : Properties of CIDR BlockDocument14 pagesClassless Inter Domain Routing (CIDR) : Properties of CIDR BlocksaraNo ratings yet
- Network AddressingDocument14 pagesNetwork AddressingbeshoyNo ratings yet
- IP Address: From Wikipedia, The Free EncyclopediaDocument9 pagesIP Address: From Wikipedia, The Free EncyclopediaAnonymous yDM6SRNo ratings yet
- Instructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Document21 pagesInstructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Honey ShineNo ratings yet
- Unit 4Document65 pagesUnit 4Durga DeviNo ratings yet
- ITN6 Students Materials Chapter7Document34 pagesITN6 Students Materials Chapter7evamNo ratings yet
- Addressing & SubnettingDocument80 pagesAddressing & SubnettingboybkaNo ratings yet
- IP AddressDocument20 pagesIP AddressNayr ZdahbNo ratings yet
- Ipv 6Document39 pagesIpv 6DEEPALI BAGULNo ratings yet
- TCP IP FundamentalsDocument11 pagesTCP IP FundamentalsMadhav ReddyNo ratings yet
- CCNA 1 Chapter 6 V4.0 AnswersDocument8 pagesCCNA 1 Chapter 6 V4.0 AnswersAbdullah Al HawajNo ratings yet
- ns-3 Direct Code Execution (DCE) Manual: Release 1.5Document67 pagesns-3 Direct Code Execution (DCE) Manual: Release 1.5meNo ratings yet
- FemtocellDocument83 pagesFemtocelljxy1600% (1)
- HUAWEI S3700 Switch DatasheetDocument12 pagesHUAWEI S3700 Switch DatasheetAlex MetalheartNo ratings yet
- 4G Wireless Systems Full Seminar Report Download (1) Computer Science Seminar TopicsDocument7 pages4G Wireless Systems Full Seminar Report Download (1) Computer Science Seminar TopicsAsad AhmadNo ratings yet
- APA v6 ExampleDocument5 pagesAPA v6 Examplethe next legendNo ratings yet
- Ov 5Document52 pagesOv 5Mangesh AbnaveNo ratings yet
- x930 Ds RevzcDocument8 pagesx930 Ds RevzcRomi JasmanNo ratings yet
- Ipv6 Addressing: Yashvant Singh Centre For Excellence in Telecom Technology and ManagementDocument45 pagesIpv6 Addressing: Yashvant Singh Centre For Excellence in Telecom Technology and ManagementRitesh SinghNo ratings yet
- What Is 4GDocument14 pagesWhat Is 4Ghi2sam007100% (1)
- Tenda Dh301 ManualDocument120 pagesTenda Dh301 ManualAm IRNo ratings yet
- Order Form - Biznet EducationnetDocument9 pagesOrder Form - Biznet EducationnetqueeeenNo ratings yet
- Literature Review Ipv6Document6 pagesLiterature Review Ipv6c5sq1b48100% (1)
- MPT-GRE: A Novel Multipath Communication Technology For The CloudDocument5 pagesMPT-GRE: A Novel Multipath Communication Technology For The Cloudhalasz_evaNo ratings yet
- Refer.3.3.4.Article - K41305885 - BIG-IP AFM DoS VectorsDocument13 pagesRefer.3.3.4.Article - K41305885 - BIG-IP AFM DoS VectorsNguyen Ho LongNo ratings yet
- TANDBERG VCS Administrator Guide (X5)Document278 pagesTANDBERG VCS Administrator Guide (X5)DimaLeshNo ratings yet
- Quidway AR19 - AR29 - AR49-VRP520-R2207L30 Release NotesDocument141 pagesQuidway AR19 - AR29 - AR49-VRP520-R2207L30 Release NotesluarcaNo ratings yet
- Security On A New Level: Zywall Usg 300/1000/2000 Zywall Usg 300/1000/2000Document6 pagesSecurity On A New Level: Zywall Usg 300/1000/2000 Zywall Usg 300/1000/2000edgar huahualuqueNo ratings yet
- Enterprise Product Portfolio (2013 Q1)Document60 pagesEnterprise Product Portfolio (2013 Q1)ปลาชุม ชุมพลNo ratings yet
- 4.3.2.6 Packet Tracer - Configuring IPv6 ACLs - ILMDocument2 pages4.3.2.6 Packet Tracer - Configuring IPv6 ACLs - ILMJorgeIvanManriqueAriasNo ratings yet
- 14-12-05 Exhibit 1 To Cisco v. Arista Copyright Infringement ComplaintDocument11 pages14-12-05 Exhibit 1 To Cisco v. Arista Copyright Infringement ComplaintFlorian MuellerNo ratings yet
- Red Hat Enterprise Linux 9: Boot Options For RHEL InstallerDocument25 pagesRed Hat Enterprise Linux 9: Boot Options For RHEL InstallerMichał GabryelskiNo ratings yet
- Module 7: Ethernet SwitchingDocument37 pagesModule 7: Ethernet SwitchingLuthfie NaufaldoNo ratings yet
- QFX5120 DatasheetDocument13 pagesQFX5120 DatasheetHmaid MohamedNo ratings yet
- FSP 150CC-GE206: Multi-Functional Ethernet Service DemarcationDocument2 pagesFSP 150CC-GE206: Multi-Functional Ethernet Service DemarcationMichael HarbuckNo ratings yet
- Usg310 16Document11 pagesUsg310 16Kiattikorn SombattoNo ratings yet
- Huawei CommunicateDocument50 pagesHuawei CommunicateEsad Ćosović EćNo ratings yet
- Xstack L3 Managed Gigabit Switches: Product HighlightsDocument10 pagesXstack L3 Managed Gigabit Switches: Product HighlightsMaycon PiettroNo ratings yet
- Otms Oxe Datasheet enDocument5 pagesOtms Oxe Datasheet enDaniel ColomboNo ratings yet
- 102-500.prepaway - Premium.exam.120q: Numbe R: 102-500 Passing Scor E: 800 Time Limi T: 120 Min File Version: 2.0Document37 pages102-500.prepaway - Premium.exam.120q: Numbe R: 102-500 Passing Scor E: 800 Time Limi T: 120 Min File Version: 2.0Sebastian Burton100% (1)
70-410 r2 Lecture Slides Lesson 10
70-410 r2 Lecture Slides Lesson 10
Uploaded by
hhhhh0 ratings0% found this document useful (0 votes)
14 views47 pagesOriginal Title
70-410_r2_lecture_slides_lesson_10
Copyright
© © All Rights Reserved
Available Formats
PPTX, PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
© All Rights Reserved
Available Formats
Download as PPTX, PDF, TXT or read online from Scribd
Download as pptx, pdf, or txt
0 ratings0% found this document useful (0 votes)
14 views47 pages70-410 r2 Lecture Slides Lesson 10
70-410 r2 Lecture Slides Lesson 10
Uploaded by
hhhhhCopyright:
© All Rights Reserved
Available Formats
Download as PPTX, PDF, TXT or read online from Scribd
Download as pptx, pdf, or txt
You are on page 1of 47
Lesson 10: Configuring
IPv4 and IPv6 Addressing
MOAC 70-410: Installing and Configuring
Windows Server 2012
Overview
• Exam Objective 4.1: Configure IPv4 and IPv6
Addressing
• IPv4 Addressing
• IPv6 Addressing
• Planning an IP Transition
© 2013 John Wiley & Sons, Inc. 2
IPv4 Addressing
Lesson 10: Configuring IPv4 and IPv6 Addressing
© 2013 John Wiley & Sons, Inc. 3
IPv4 Addressing
• IP Address
o 32-bit address
o Four 8-bit decimal values between 0 and 255 separated by
periods (octets)
• Subnet Mask
o 32-bit value of 0’s and 1’s
o 1’s designate network bits, 0’s are host bits
Network Host
Examples: IP Address 192.168.43.100
Subnet Mask 255.255.255.0
© 2013 John Wiley & Sons, Inc. 4
IPv4 Classful Addressing
The three IPv4 address classes
© 2013 John Wiley & Sons, Inc. 5
IPv4 Address Classes
IP Address Class Class A Class B Class C
First bit values (binary) 0 10 110
First byte value (decimal) 0–127 128–191 192–223
Number of network identifier bits 8 16 24
Number of host identifier bits 24 16 8
Number of possible networks 126 16,384 2,097,152
Number of possible hosts 16,777,214 65,534 254
© 2013 John Wiley & Sons, Inc. 6
Classless Inter-Domain
Routing
• Classful addressing was gradually phased out by a
series of subnetting methods, including variable
length subnet masking (VLSM) and, eventually,
Classless Inter-Domain Routing (CIDR).
• CIDR is a subnetting method that enables
administrators to place the division between the
network bits and the host bits anywhere in the
address, not just between octets.
© 2013 John Wiley & Sons, Inc. 7
CIDR
CIDR notation: 192.168.43.0/26
• Where the /26 means 26 bits of the address are used
as the network identifier
• In binary, the subnet mask translates to:
11111111.11111111.1111111.11000000
or 255.255.255.192 in decimal
• This would allow us to divide this address into 4
networks, each with up to 62 hosts
© 2013 John Wiley & Sons, Inc. 8
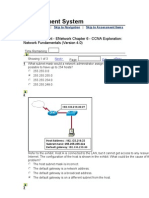
CIDR 192.168.43.0/26
Networks
Network Starting IP Ending IP
Subnet Mask
Address Address Address
192.168.43.0 192.168.43.1 192.168.43.62 255.255.255.192
192.168.43.64 192.168.43.65 192.168.43.126 255.255.255.192
192.168.43.128 192.168.43.129 192.168.43.190 255.255.255.192
192.168.43.192 192.168.43.193 192.168.43.254 255.255.255.192
© 2013 John Wiley & Sons, Inc. 9
Public and Private
IPv4 Addressing
• Registered IP addresses are not necessary for
workstations that merely access resources on the
Internet
• The three blocks of addresses allocated for private
use are as follows:
o 10.0.0.0/8
o 172.16.0.0/12
o 192.168.0.0/16
© 2013 John Wiley & Sons, Inc. 10
IPv4 Subnetting
• Allows you to split one IP address range into multiple networks (e.g., you
can take the 10.0.0.0/8 private IP address range and use the entire second
octet as a subnet ID).
• This creates up to 256 subnets with up to 65,536 hosts.
• The subnet masks will be 255.255.0.0 and the network addresses will
proceed as follows:
o 10.0.0.0/16
o 10.1.0.0/16
o 10.2.0.0/16
o …
o 10.255.0.0/16
• When you are working on an existing network, the subnetting process is
more difficult.
© 2013 John Wiley & Sons, Inc. 11
Calculate IPv4 Subnets
1. Determine how many subnet identifier bits you need to create
the required number of subnets.
2. Subtract the subnet bits you need from the host bits and add
them to the network bits.
3. Calculate the subnet mask by adding the network and subnet
bits in binary form and converting the binary value to decimal.
4. Take the least significant subnet bit and the host bits, in binary
form, and convert them to a decimal value.
5. Increment the network identifier (including the subnet bits) by
the decimal value you calculated to determine the network
addresses of your new subnets.
© 2013 John Wiley & Sons, Inc. 12
Supernetting
• Allows contiguous networks to be added to a routing table
with one entry to reduce the size of Internet routing tables.
• For example:
172.16.43.0/24
172.16.44.0/24
172.16.45.0/24
172.16.46.0/24
172.16.47.0/24
• Can all be expressed in one supernet address:
172.16.40.0/21
© 2013 John Wiley & Sons, Inc. 13
Assigning IPv4 Addresses
To assign IPv4 addresses, there are three basic methods:
• Manual configuration
• Dynamic Host Configuration Protocol (DHCP)
• Automatic Private IP Addressing (APIPA)
© 2013 John Wiley & Sons, Inc. 14
Manual IPv4 Address
Configuration
• Manually enter IP address, subnet mask, default
gateway and DNS servers.
• Use a GUI or command line.
• Not difficult, but it can be time consuming on a large
network.
• Difficult to troubleshoot if information is entered
incorrectly.
© 2013 John Wiley & Sons, Inc. 15
Dynamic Host Configuration
Protocol (DHCP)
• Client computers are configured to Obtain an IP
address automatically.
• DHCP Servers on the network contain a pool of
addresses and other IPv4 configuration.
• Clients request configuration at boot up.
• DHCP Servers respond to the requests.
• IPv4 configurations are leased for a period of time
and renewed as necessary.
• No addresses are duplicated.
© 2013 John Wiley & Sons, Inc. 16
Assigning IPv4 Addresses
The Internet Protocol Version 4 (TCP/IPv4)
Properties sheet
© 2013 John Wiley & Sons, Inc. 17
Automatic Private IP
Addressing (APIPA)
• A DHCP failover mechanism used by all current
Microsoft Windows operating systems.
• If a system fails to locate a DHCP server on the
network, APIPA takes over and automatically assigns
an address on the 169.254.0.0/16 network to the
computer.
• For a small network that consists of only a single
LAN, APIPA is a simple and effective alternative to
installing a DHCP server.
© 2013 John Wiley & Sons, Inc. 18
IPv6 Addressing
Lesson 10: Configuring IPv4 and IPv6 Addressing
© 2013 John Wiley & Sons, Inc. 19
IPv6 Addressing
• Designed to increase the size of the IP address space
(128 bit), thus providing addresses for many more
devices than IPv4
• Reduces the size of the routing tables because the size
of the addresses provides for more than the two levels
of subnetting currently possible with IPv4
© 2013 John Wiley & Sons, Inc. 20
Introducing IPv6
• IPv6 addresses use a notation called colon-
hexadecimal format
• Eight 16-bit hexadecimal numbers, separated by
colons:
XX:XX:XX:XX:XX:XX:XX:XX
• Each X represents eight bits (or 1 byte), which in
hexadecimal notation is represented by two
characters, as in:
21cd:0053:0000:0000:e8bb:04f2:003c:c394
© 2013 John Wiley & Sons, Inc. 21
Contracting IPv6
Addresses
• When an IPv6 address has two or more consecutive
eight-bit blocks of zeroes, you can replace them with
a double colon (but you can only use one double
colon in any IPv6 address):
21cd:0053::e8bb:04f2:003c:c394
• You can also remove the leading zeros in any block
where they appear:
21cd:53::e8bb:4f2:3c:c394
© 2013 John Wiley & Sons, Inc. 22
Expressing IPv6
Network Addresses
• No subnet masks in IPv6
• Network addresses use the same slash notation as
CIDR:
21cd:53::/64
• This is the contracted form for the following network
address:
21cd:0053:0000:0000/64
© 2013 John Wiley & Sons, Inc. 23
IPv6 Address Types
IPv6 supports three address types:
• Unicast: Provides one-to-one transmission service to
individual interfaces, including server farms sharing a single
address. IPv6 supports several types of unicast addresses,
including global, link-local, and unique local.
• Multicast: Provides one-to-many transmission service to
groups of interfaces identified by a single multicast address.
• Anycast: Provides one-to-one-of-many transmission service
to groups of interfaces, only the nearest of which (measured
by the number of intermediate routers) receives the
transmission.
© 2013 John Wiley & Sons, Inc. 24
Global
Unicast Addresses
The current official format for global unicast addresses
consists of the following elements:
• Global routing prefix: A 48-bit field beginning with
the 001 FP value, the hierarchical structure of which
is left up to the RIR
• Subnet ID: Formerly known as the SLA, a 16-bit
field that organizations can use to create an internal
hierarchy of sites or subnets
• Interface ID: A 64-bit field identifying a specific
interface on the network
© 2013 John Wiley & Sons, Inc. 25
Global Unicast Addresses
The current IPv6 global unicast address format
© 2013 John Wiley & Sons, Inc. 26
Subnet IDs
Organizations have a16-bit subnet ID with which to create an
internal subnet hierarchy, if desired. Here are some of the
possible subnetting options:
o One-level subnet: By setting all subnet ID bits to 0, all computers in
the organization are part of a single subnet. This option is only
suitable for smaller organizations.
o Two-level subnet: By creating a series of 16-bit values, you can split
the network into as many as 65,536 subnets. This is the functional
equivalent of IPv4 subnetting, but with a much larger subnet address
space.
o Multi-level subnet: By allocating specific numbers of subnet ID bits,
you can create multiple levels of subnets, sub-subnets, and sub-sub-
subnets; suitable for an enterprise of almost any size.
© 2013 John Wiley & Sons, Inc. 27
Subnet ID Example
To support a large international enterprise, you could split the subnet ID as
follows:
• Country (4 bits): Creates up to 16 subnets representing countries in which
the organization has offices
• State (6 bits): Creates up to 64 sub-subnets within each country,
representing states, provinces, or other geographical divisions
• Office (2 bits): Creates up to 4 sub-sub-subnets within each state or
province, representing offices located in various cities
• Department (4 bits): Creates up to 16 sub-sub-sub-subnets within each
office, representing the various departments or divisions.
To create a subnet ID for a particular office, it is up to the enterprise
administrators to assign values for each field.
© 2013 John Wiley & Sons, Inc. 28
Interface IDs
• The interface ID contains a unique identifier for a specific
interface on the network.
• The Institute for Electrical and Electronic Engineers (IEEE)
defines the format for the 48-bit MAC address assigned to
each network adapter by the manufacturer, as well as the
EUI-64 identifier format derived from it.
• A privacy problem with this method of deriving interface
IDs from the computer’s hardware—the location of a mobile
computer might be tracked based on its IPv6 address.
• Instead of using MAC addresses, Windows operating
systems generate random interface IDs by default.
© 2013 John Wiley & Sons, Inc. 29
Link-Local
Unicast Addresses
• In IPv6, systems that assign themselves an address
automatically create a link-local unicast address,
which is the equivalent of an APIPA address in IPv4.
• All link local addresses have the same network
identifier: a 10-bit FP of 11111110 010 followed by 54
zeroes, resulting in:
fe80:0000:0000:0000/64
• In its more compact form, the link-local network
address is:
fe80::/64
© 2013 John Wiley & Sons, Inc. 30
Unique Local
Unicast Addresses
These are the same as private addresses in IPv4, with the
following format:
• Global ID: A 48-bit field beginning with an 8-bit FP
of 11111101 in binary, or fd00::/8 in hexadecimal. The
remaining 40 bits of the global ID are randomly
generated.
• Subnet ID: A 16-bit field that organizations can use
to create an internal hierarchy of sites or subnets.
• Interface ID: A 64-bit field identifying a specific
interface on the network.
© 2013 John Wiley & Sons, Inc. 31
Unique Local Unicast Addresses
The IPv6 unique local unicast address format
© 2013 John Wiley & Sons, Inc. 32
Special Addresses
• Loopback address: Any messages sent to it are
returned back to the sending system.
0:0:0:0:0:0:0:1 or ::1
• Unspecified address: The address the system uses
while requesting an address from a DHCP server.
0:0:0:0:0:0:0:0
© 2013 John Wiley & Sons, Inc. 33
Multicast Addresses
Multicast addresses always begin with an FP value of 11111111, in
binary, or ff in hexadecimal. The entire multicast address format is as
follows:
• FP: An 8-bit field that identifies the message as a multicast.
• Flags: A 4-bit field that specifies whether the multicast address
contains the address of a rendezvous point (0111), is based on a
network prefix (0010), and is permanent (0000) or transient (0001).
• Scope: A 4-bit field that specifies how widely routers can forward the
address. Values include interface-local (0001), link-local (0010), site-
local (0101), organization-local (1000), and global (1110).
• Group ID: A 112-bit field uniquely identifying a multicast group.
© 2013 John Wiley & Sons, Inc. 34
Anycast Addresses
• Used to identify the routers within a given address
scope and send traffic to the nearest router, as
determined by the local routing protocols.
• Can be used to identify a particular set of routers in
the enterprise, such as those that provide access to the
Internet.
• To use anycasts, the routers must be configured to
recognize the anycast addresses.
© 2013 John Wiley & Sons, Inc. 35
Assigning IPv6 Addresses
As with IPv4, a Windows computer can obtain an IPv6
address by three possible methods:
• Manual allocation: A user or administrator manually
supplies an address and other information for each
network interface.
• Self-allocation: The computer creates its own address
using a process called stateless address autoconfiguration.
• Dynamic allocation: The computer solicits and receives
an address from a Dynamic Host Configuration Protocol
(DHCPv6) server on the network.
© 2013 John Wiley & Sons, Inc. 36
Assigning IPv6 Addresses
The Internet Protocol Version 6 (TCP/IPv6)
Properties sheet
© 2013 John Wiley & Sons, Inc. 37
Planning an IP Transition
Lesson 10: Configuring IPv4 and IPv6 Addressing
© 2013 John Wiley & Sons, Inc. 38
Planning an IP Transition
• Administrators are reluctant to change from IPv4 to
IPv6 because there is a lot to learn.
• IPv4 hardware is still functioning.
• The Internet is still mostly IPv4, but there is a gradual
transition happening where there will be support for
both IP versions.
• Currently, we must have mechanisms in place to
transmit IPv6 traffic over IPv4 connections, but the
situation will be reversed in the future.
© 2013 John Wiley & Sons, Inc. 39
Using a Dual IP Stack
• The simplest way to transition is to run both IP
versions.
• Windows has been doing this since Windows Server
2008 and Windows Vista.
• Use ipconfig /all to see IPv6 configuration.
• This allows us to communicate with IPv4 and IPv6
devices at the same time.
© 2013 John Wiley & Sons, Inc. 40
Tunneling
• Tunneling is the process by which a system
encapsulates an IPv6 datagram within an IPv4 packet.
• Often used for router-to-router communication when
communicating between two IPv6 networks over an
IPv4 connection.
© 2013 John Wiley & Sons, Inc. 41
Tunneling
Two IPv6 networks connected by an IPv4 tunnel
© 2013 John Wiley & Sons, Inc. 42
Configuring Tunnels
Manually
• It is possible to manually create semi-permanent tunnels that carry
IPv6 traffic through an IPv4-only network. When a computer
running Windows Server 2012 R2 or Windows 8 is functioning as
one end of the tunnel, you can use this command:
netsh interface ipv6 add v6v4tunnel “interface”
localaddress remoteaddress
• In this command, interface is a friendly name you want to assign to
the tunnel you are creating and localaddress and remoteaddress are
the IPv4 addresses forming the two ends of the tunnel. An example
of an actual command would be this:
netsh interface ipv6 add v6v4tunnel “tunnel”
206.73.118.19 157.54.206.43
© 2013 John Wiley & Sons, Inc. 43
Configuring Tunnels
Automatically
A number of mechanisms automatically create tunnels over IPv4
connections. These technologies are designed to be temporary
solutions during the IPv4-to-IPv6 transition:
• 6to4: Incorporates the IPv4 connections in a network into the IPv6
infrastructure by defining a method for expressing IPv4 addresses in
IPv6 format and encapsulating IPv6 traffic into IPv4 packets.
• ISATAP (Intra-Site Automatic Tunnel Addressing Protocol): An
automatic tunneling protocol used by the Windows workstation
operating systems that emulates an IPv6 link using an IPv4 network.
• Teredo: A mechanism that addresses the issue of NAT routers not
supporting 6to4 by enabling devices behind non-IPv6 NAT routers to
function as tunnel endpoints.
© 2013 John Wiley & Sons, Inc. 44
Lesson Summary
• The IPv4 address space consists of 32-bit addresses, notated as four 8-bit
decimal values from 0 to 255, separated by periods (e.g., 192.168.43.100).
This is known as dotted decimal notation, and the individual 8-bit decimal
values are called octets or bytes.
• Because the subnet mask associated with IP addresses can vary, so can the
number of bits used to identify the network and the host. The original
Internet Protocol (IP) standard defines three address classes for assignment
to networks, which support different numbers of networks and hosts.
• Because of its wastefulness, classful addressing was gradually made
obsolete by a series of subnetting methods, including variable-length subnet
masking (VLSM) and eventually Classless Inter-Domain Routing (CIDR).
CIDR is a subnetting method that enables administrators to place the
division between the network bits and the host bits anywhere in the address,
not just between octets.
© 2013 John Wiley & Sons, Inc. 45
Lesson Summary
• When a Windows computer starts, it initiates the IPv6
stateless address autoconfiguration process, during which
it assigns each interface a link-local unicast address.
• The simplest and most obvious method for transitioning
from IPv4 to IPv6 is to run both, and this is what all
current versions of Windows do.
• The primary method for transmitting IPv6 traffic over an
IPv4 network is called tunneling—the process by which a
system encapsulates an IPv6 datagram within an IPv4
packet.
© 2013 John Wiley & Sons, Inc. 46
Copyright 2013 John Wiley & Sons, Inc.
All rights reserved. Reproduction or translation of this work beyond that
named in Section 117 of the 1976 United States Copyright Act without the
express written consent of the copyright owner is unlawful. Requests for
further information should be addressed to the Permissions Department, John
Wiley & Sons, Inc. The purchaser may make back-up copies for his/her own
use only and not for distribution or resale. The Publisher assumes no
responsibility for errors, omissions, or damages, caused by the use of these
programs or from the use of the information contained herein.
You might also like
- Practice Testanswers 6Document6 pagesPractice Testanswers 6Marina GeorgiouNo ratings yet
- Data Comm Part 2.ppt NewDocument48 pagesData Comm Part 2.ppt Newmuhabamohamed21No ratings yet
- CH5Document58 pagesCH5digafeeyuelNo ratings yet
- IP AddressingDocument29 pagesIP AddressingcsebitannaNo ratings yet
- CCNA1 Chapter 6Document6 pagesCCNA1 Chapter 6mubaswirNo ratings yet
- IPv4 ReportDocument34 pagesIPv4 ReportGWYNETH DIOGRACIASNo ratings yet
- Chapter 4 Part IDocument86 pagesChapter 4 Part Ianebek555No ratings yet
- IP Addressing: Introductory MaterialDocument26 pagesIP Addressing: Introductory MaterialRajurajiNo ratings yet
- Mod 03Document56 pagesMod 03michael.santiago15No ratings yet
- Unit 4. NetworkingDocument31 pagesUnit 4. Networkingbca2022jagranNo ratings yet
- CN Unit 2Document49 pagesCN Unit 2Prakhar MishraNo ratings yet
- 98-366 MVA Slides Lesson 4Document31 pages98-366 MVA Slides Lesson 4cvigaNo ratings yet
- CCNA1 Chapter 6 Practice Test Questions: SW 7/31/2012 /var/www/apps/conversion/current/tmp/scratch430/105029902.doc 1Document6 pagesCCNA1 Chapter 6 Practice Test Questions: SW 7/31/2012 /var/www/apps/conversion/current/tmp/scratch430/105029902.doc 1Ramel PoliusNo ratings yet
- Chapter 4 Part 1Document25 pagesChapter 4 Part 1FantaNo ratings yet
- CCNA1 Chap6 Practice TestquestionsDocument6 pagesCCNA1 Chap6 Practice TestquestionsAnhTuan LeNo ratings yet
- IPV4 and IPV6: Presented by Ye Kyaw Thein M.SC (Physics), M.I.ScDocument41 pagesIPV4 and IPV6: Presented by Ye Kyaw Thein M.SC (Physics), M.I.ScMie NgeNo ratings yet
- L06 NetworkLayer PartIIDocument54 pagesL06 NetworkLayer PartIITerence YapNo ratings yet
- Instructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Document28 pagesInstructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Nuhamin BirhanuNo ratings yet
- Chapter 4 Part I - 220121001702Document86 pagesChapter 4 Part I - 220121001702zerihun nanaNo ratings yet
- 3 IPv4 Part2Document38 pages3 IPv4 Part2Easha AsifNo ratings yet
- IP Addressing: Introductory MaterialDocument26 pagesIP Addressing: Introductory MaterialAamer ZahoorNo ratings yet
- Adresarea IPDocument80 pagesAdresarea IPgheorghe_georgelNo ratings yet
- File 034Document25 pagesFile 034Zulkernain Omer TariqNo ratings yet
- ITN instructorPPT Chapter8Document88 pagesITN instructorPPT Chapter8Paul BryanNo ratings yet
- Advanced IP AddressingDocument14 pagesAdvanced IP AddressingVictor BittarNo ratings yet
- Module 11: Ipv4 AddressingDocument44 pagesModule 11: Ipv4 AddressingLuthfie NaufaldoNo ratings yet
- NB instructorPPT Chapter7 FinalDocument89 pagesNB instructorPPT Chapter7 FinalSergio MedinaNo ratings yet
- Ip AddressingDocument83 pagesIp AddressingGetnete degemuNo ratings yet
- BEnny AzDocument8 pagesBEnny AzastaylerrNo ratings yet
- IP Addressing: (Ipv4 Addresses)Document35 pagesIP Addressing: (Ipv4 Addresses)Kumail RazaNo ratings yet
- NDC Chapter 1Document10 pagesNDC Chapter 1Miraj SherifNo ratings yet
- CN - Chapter 5 - The Network Layer - Class 3, 4Document24 pagesCN - Chapter 5 - The Network Layer - Class 3, 4himanshuajaypandeyNo ratings yet
- IPV4 and Subnetting StrategyDocument39 pagesIPV4 and Subnetting StrategyrolandsabitNo ratings yet
- chapter3-IP AddressingDocument47 pageschapter3-IP AddressingmulugetaNo ratings yet
- IP Addressing: Presentation - ID © 2008 Cisco Systems, Inc. All Rights Reserved. Cisco ConfidentialDocument40 pagesIP Addressing: Presentation - ID © 2008 Cisco Systems, Inc. All Rights Reserved. Cisco Confidentialnathaniel manuzonNo ratings yet
- Introduction To Ip AddressDocument22 pagesIntroduction To Ip AddressMetsi KinNo ratings yet
- Take Assessment - Enetwork Chapter 6 - Ccna Exploration: Network Fundamentals (Version 4.0) - Answers - 2012 - 2013Document7 pagesTake Assessment - Enetwork Chapter 6 - Ccna Exploration: Network Fundamentals (Version 4.0) - Answers - 2012 - 2013Alexander Henao GutierrezNo ratings yet
- Network Subnetting 4 PDFDocument6 pagesNetwork Subnetting 4 PDFEdison Jr. GaudicosNo ratings yet
- CN Lab 3Document12 pagesCN Lab 3talha khalidNo ratings yet
- Network ConfigurationDocument22 pagesNetwork Configurationapi-556424124No ratings yet
- ReS1.08 IP ADDRESSING ARCHITECTUREDocument14 pagesReS1.08 IP ADDRESSING ARCHITECTUREHisham MohamedNo ratings yet
- Ip AddressingDocument38 pagesIp AddressingFadilMaulanahNo ratings yet
- CCNA 1 v3.0 Module 9 TCP/IP Protocol Suite and IP AddressingDocument33 pagesCCNA 1 v3.0 Module 9 TCP/IP Protocol Suite and IP AddressingPŘincê ÂĻĩNo ratings yet
- Lec 7 - IP AddressDocument60 pagesLec 7 - IP AddressMUBEEN LIAQATNo ratings yet
- Ipv4 Con GurationDocument5 pagesIpv4 Con GurationLaura DeeNo ratings yet
- Chapter - 7Document99 pagesChapter - 7Sindhu official radhakrishnNo ratings yet
- Classless Inter Domain Routing (CIDR) : Properties of CIDR BlockDocument14 pagesClassless Inter Domain Routing (CIDR) : Properties of CIDR BlocksaraNo ratings yet
- Network AddressingDocument14 pagesNetwork AddressingbeshoyNo ratings yet
- IP Address: From Wikipedia, The Free EncyclopediaDocument9 pagesIP Address: From Wikipedia, The Free EncyclopediaAnonymous yDM6SRNo ratings yet
- Instructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Document21 pagesInstructor Materials Chapter 7: IP Addressing: CCNA Routing and Switching Introduction To Networks v6.0Honey ShineNo ratings yet
- Unit 4Document65 pagesUnit 4Durga DeviNo ratings yet
- ITN6 Students Materials Chapter7Document34 pagesITN6 Students Materials Chapter7evamNo ratings yet
- Addressing & SubnettingDocument80 pagesAddressing & SubnettingboybkaNo ratings yet
- IP AddressDocument20 pagesIP AddressNayr ZdahbNo ratings yet
- Ipv 6Document39 pagesIpv 6DEEPALI BAGULNo ratings yet
- TCP IP FundamentalsDocument11 pagesTCP IP FundamentalsMadhav ReddyNo ratings yet
- CCNA 1 Chapter 6 V4.0 AnswersDocument8 pagesCCNA 1 Chapter 6 V4.0 AnswersAbdullah Al HawajNo ratings yet
- ns-3 Direct Code Execution (DCE) Manual: Release 1.5Document67 pagesns-3 Direct Code Execution (DCE) Manual: Release 1.5meNo ratings yet
- FemtocellDocument83 pagesFemtocelljxy1600% (1)
- HUAWEI S3700 Switch DatasheetDocument12 pagesHUAWEI S3700 Switch DatasheetAlex MetalheartNo ratings yet
- 4G Wireless Systems Full Seminar Report Download (1) Computer Science Seminar TopicsDocument7 pages4G Wireless Systems Full Seminar Report Download (1) Computer Science Seminar TopicsAsad AhmadNo ratings yet
- APA v6 ExampleDocument5 pagesAPA v6 Examplethe next legendNo ratings yet
- Ov 5Document52 pagesOv 5Mangesh AbnaveNo ratings yet
- x930 Ds RevzcDocument8 pagesx930 Ds RevzcRomi JasmanNo ratings yet
- Ipv6 Addressing: Yashvant Singh Centre For Excellence in Telecom Technology and ManagementDocument45 pagesIpv6 Addressing: Yashvant Singh Centre For Excellence in Telecom Technology and ManagementRitesh SinghNo ratings yet
- What Is 4GDocument14 pagesWhat Is 4Ghi2sam007100% (1)
- Tenda Dh301 ManualDocument120 pagesTenda Dh301 ManualAm IRNo ratings yet
- Order Form - Biznet EducationnetDocument9 pagesOrder Form - Biznet EducationnetqueeeenNo ratings yet
- Literature Review Ipv6Document6 pagesLiterature Review Ipv6c5sq1b48100% (1)
- MPT-GRE: A Novel Multipath Communication Technology For The CloudDocument5 pagesMPT-GRE: A Novel Multipath Communication Technology For The Cloudhalasz_evaNo ratings yet
- Refer.3.3.4.Article - K41305885 - BIG-IP AFM DoS VectorsDocument13 pagesRefer.3.3.4.Article - K41305885 - BIG-IP AFM DoS VectorsNguyen Ho LongNo ratings yet
- TANDBERG VCS Administrator Guide (X5)Document278 pagesTANDBERG VCS Administrator Guide (X5)DimaLeshNo ratings yet
- Quidway AR19 - AR29 - AR49-VRP520-R2207L30 Release NotesDocument141 pagesQuidway AR19 - AR29 - AR49-VRP520-R2207L30 Release NotesluarcaNo ratings yet
- Security On A New Level: Zywall Usg 300/1000/2000 Zywall Usg 300/1000/2000Document6 pagesSecurity On A New Level: Zywall Usg 300/1000/2000 Zywall Usg 300/1000/2000edgar huahualuqueNo ratings yet
- Enterprise Product Portfolio (2013 Q1)Document60 pagesEnterprise Product Portfolio (2013 Q1)ปลาชุม ชุมพลNo ratings yet
- 4.3.2.6 Packet Tracer - Configuring IPv6 ACLs - ILMDocument2 pages4.3.2.6 Packet Tracer - Configuring IPv6 ACLs - ILMJorgeIvanManriqueAriasNo ratings yet
- 14-12-05 Exhibit 1 To Cisco v. Arista Copyright Infringement ComplaintDocument11 pages14-12-05 Exhibit 1 To Cisco v. Arista Copyright Infringement ComplaintFlorian MuellerNo ratings yet
- Red Hat Enterprise Linux 9: Boot Options For RHEL InstallerDocument25 pagesRed Hat Enterprise Linux 9: Boot Options For RHEL InstallerMichał GabryelskiNo ratings yet
- Module 7: Ethernet SwitchingDocument37 pagesModule 7: Ethernet SwitchingLuthfie NaufaldoNo ratings yet
- QFX5120 DatasheetDocument13 pagesQFX5120 DatasheetHmaid MohamedNo ratings yet
- FSP 150CC-GE206: Multi-Functional Ethernet Service DemarcationDocument2 pagesFSP 150CC-GE206: Multi-Functional Ethernet Service DemarcationMichael HarbuckNo ratings yet
- Usg310 16Document11 pagesUsg310 16Kiattikorn SombattoNo ratings yet
- Huawei CommunicateDocument50 pagesHuawei CommunicateEsad Ćosović EćNo ratings yet
- Xstack L3 Managed Gigabit Switches: Product HighlightsDocument10 pagesXstack L3 Managed Gigabit Switches: Product HighlightsMaycon PiettroNo ratings yet
- Otms Oxe Datasheet enDocument5 pagesOtms Oxe Datasheet enDaniel ColomboNo ratings yet
- 102-500.prepaway - Premium.exam.120q: Numbe R: 102-500 Passing Scor E: 800 Time Limi T: 120 Min File Version: 2.0Document37 pages102-500.prepaway - Premium.exam.120q: Numbe R: 102-500 Passing Scor E: 800 Time Limi T: 120 Min File Version: 2.0Sebastian Burton100% (1)